The hacker metabolized by domination
Popularized by cyberpunk literature, the hacker figure has emerged over the last three decades as a possible embodiment of resistance to the domination of monopolistic technology companies. Dressed in black, hooded on the head and introverted, the hacker has become a commonplace in the field of contemporary art. The call for repoliticization to deal with the neoliberal “strategy of shock” finds with it a figure that seems legitimate, so much so that the action of “hacker” has extended far beyond the field of computer programming to designate all the incidental practices of diversion: using the tools of the system against itself, using the flaws, infiltrating it.
This generalization of the hacker paradigm conceals the hacker’s concrete ambivalence. Indeed, if it seems at first sight to oppose domination by diverting the tools and platforms set up by it, this diversion is desired by its object. By detecting vulnerabilities, we can fix them and these vulnerabilities allow us to develop a software narrative that captivates the public. Indeed, we notice that when a security breach is spotted, it makes the headlines of the media.
This metabolization of the fault, immediately ingested by domination, also takes an economic form since many hackers, after some exploits, work for companies specialized in computer security. This hacking activity is accepted and financed by the companies, because it allows not only to add corrections to software, but also to make known the activities of the company by showing them according to an almost living fragility.

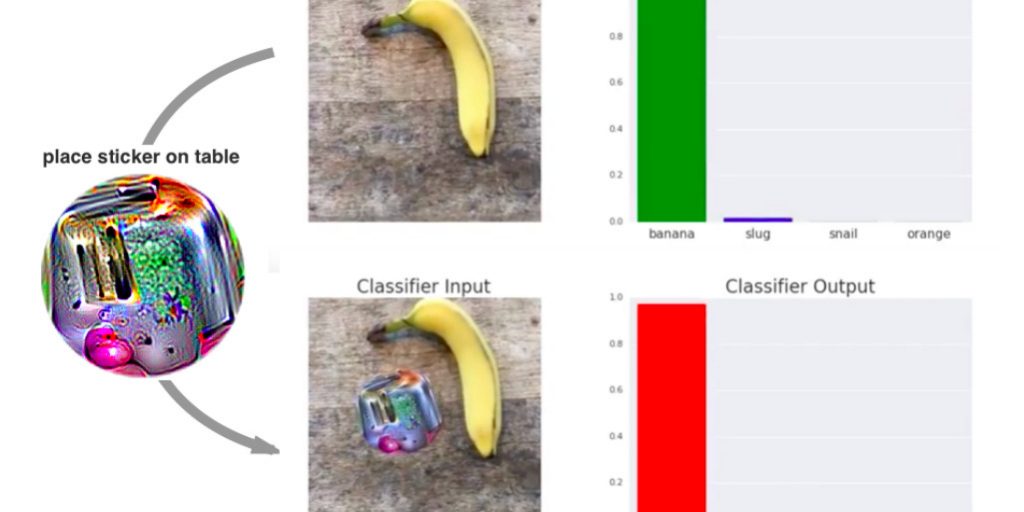
A recent example of this economic and ideological metabolization of diversion is the development by Google researchers of a sticker to deceive the visual recognition operated by “deep learning” (https://arxiv.org/pdf/1712.09665.pdf). It is amusing to notice that some artists-hackers have relayed this information, as if it contained the possibility of resisting the development of AI (there is also a quasi-domain of stickers that bankrupt automated recognition, see https://www.alternet.org/news-amp-politics/anti-surveillance-state-clothes-and-gadgets-block-face-recognition-technology). However, this resistance, far from being external to domination, is internalised (in the sense of an intern). It is a resistance in the electrical sense of the term, as in the case of growth hacker (https://fr.wikipedia.org/wiki/Growth_Hacking). In addition, it often has the objective of defending privacy. But its development can be analyzed from a historical point of view as being convergent with the development of capitalism according to a certain figure of sovereign subjectivity.
The social and political structure of this metabolization was finely analyzed by Alexander R. Galloway, Eugene Thacker in The Exploit (2007) and demonstrates that diversion is desired by social platforms as an opportunity for improvement and symbolic appropriation. Domination is not hierarchical here, it is presented in a horizontal and rhizomatic form, so that diversion in general, transgression, the logic of accident and resistance (see the video of Deleuze’s Abécédaire on this subject which has become a meme) become active participants in the leisure activities of the system of domination.
